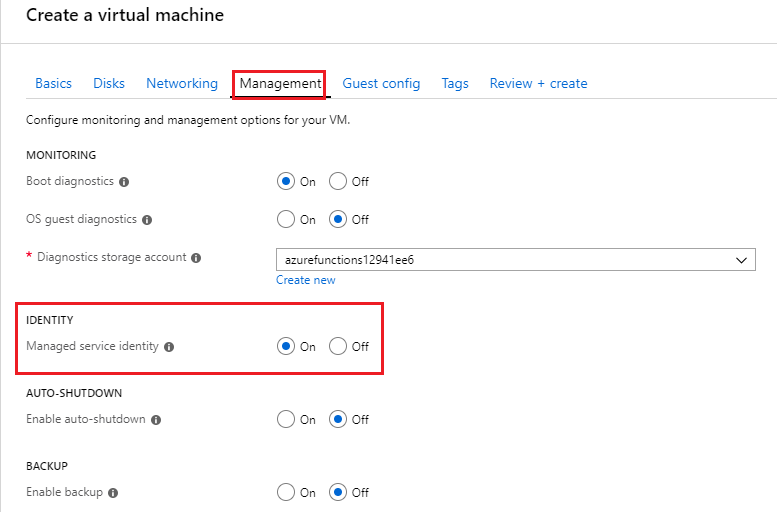
System Assigned Managed Identity
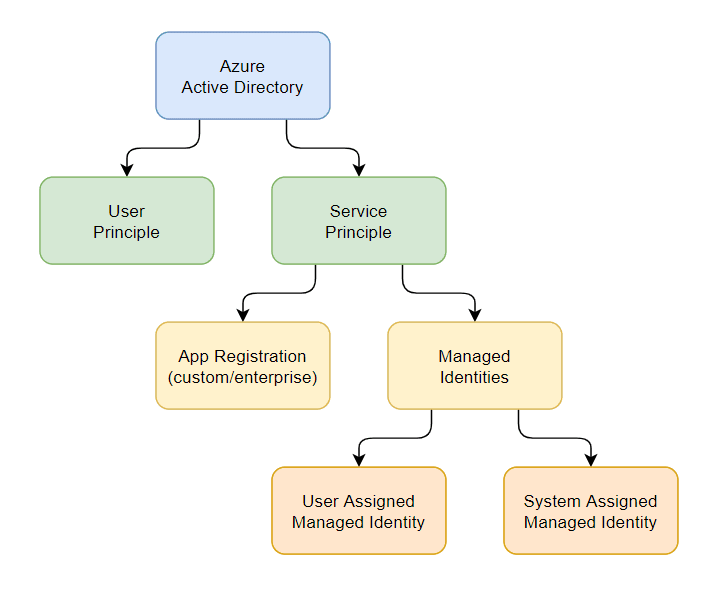
System assigned managed identity. There are two types of managed identities. Deploy Service Fabric application with system-assigned managed identity. It is deleted automatically at.
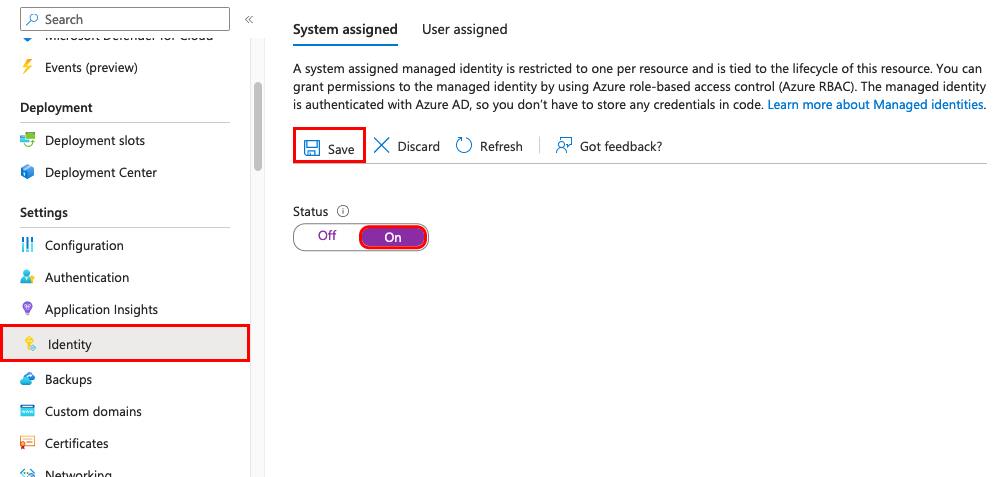
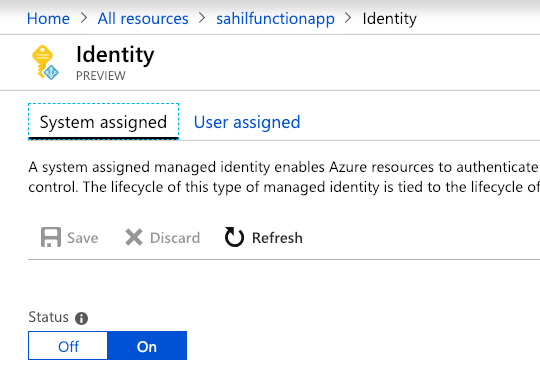
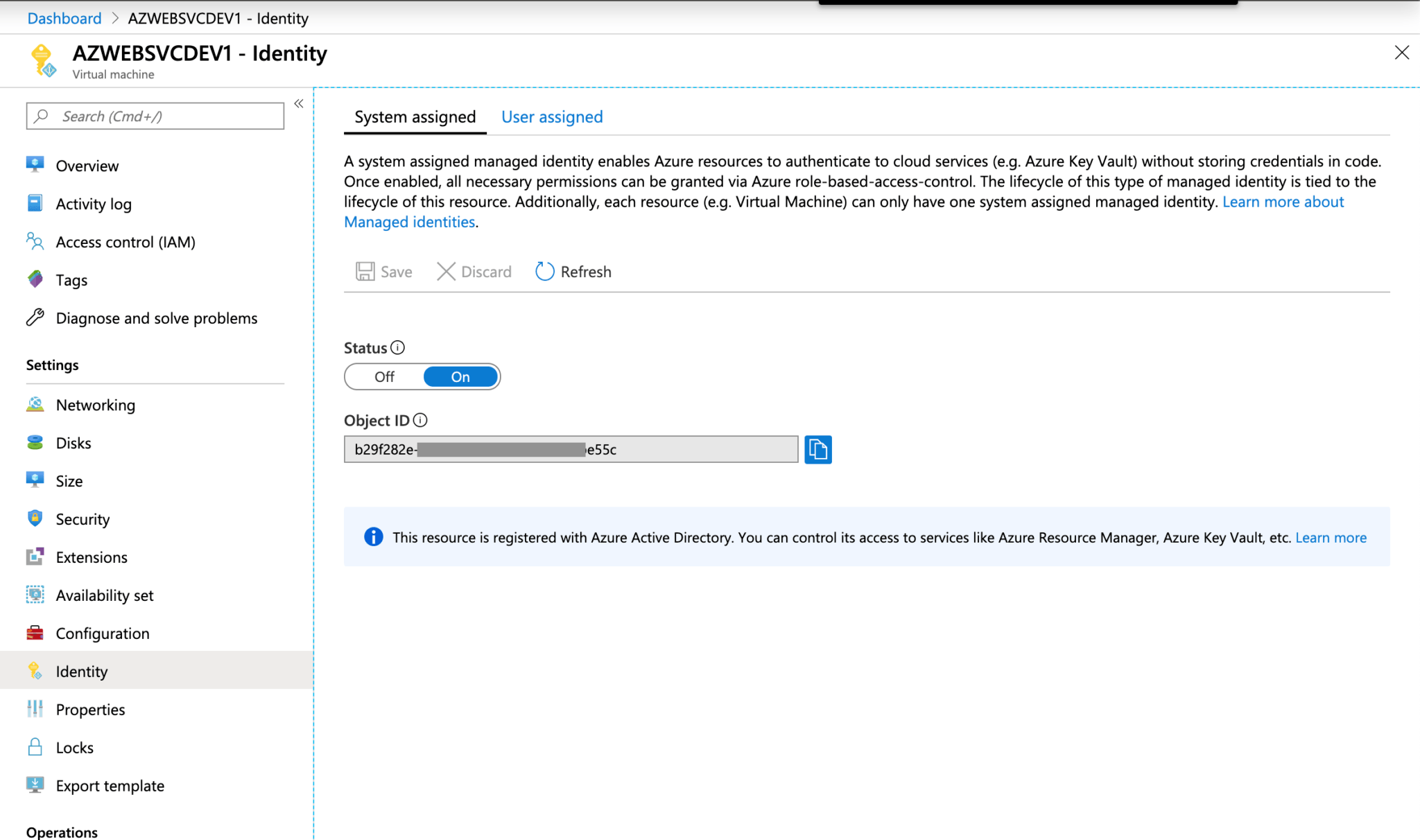
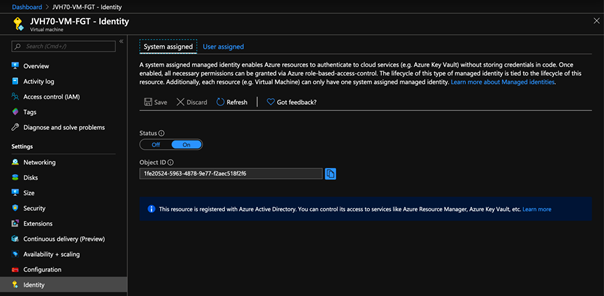
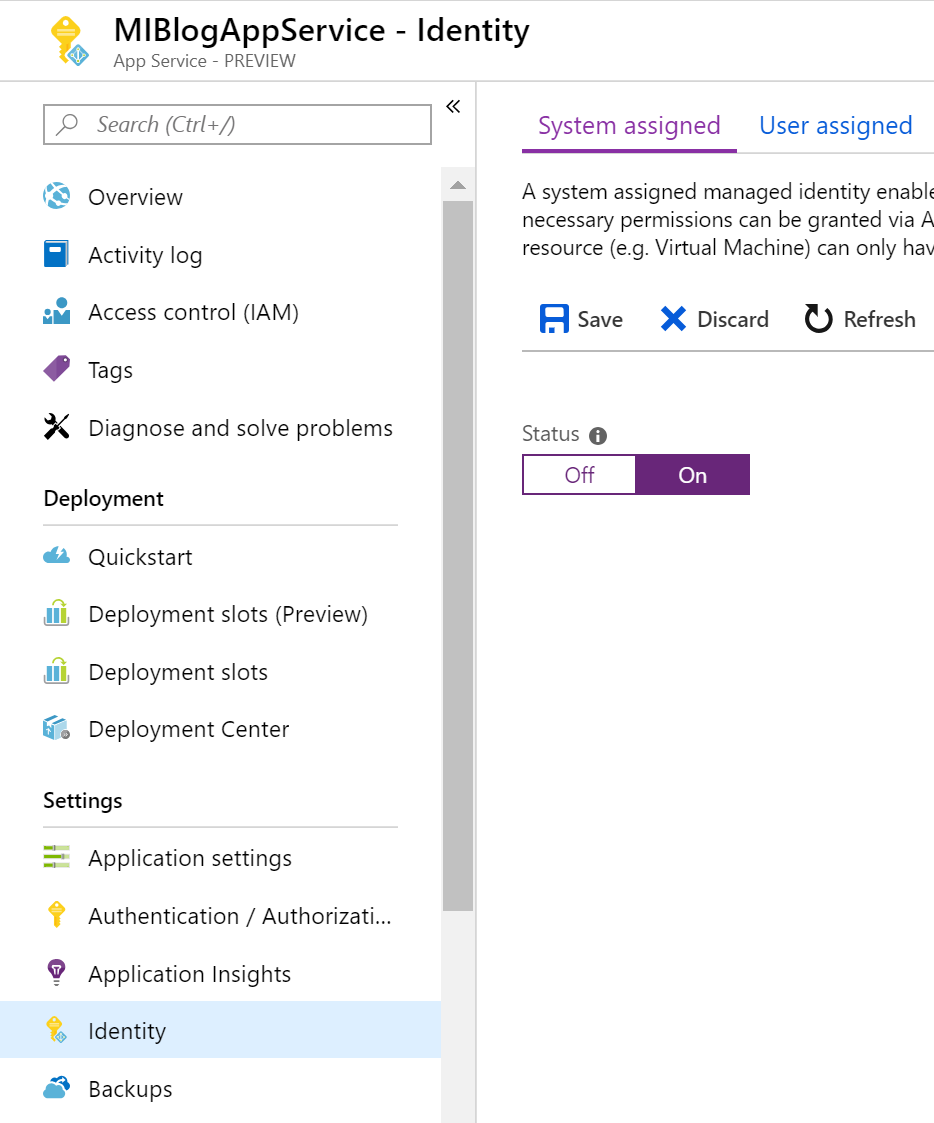
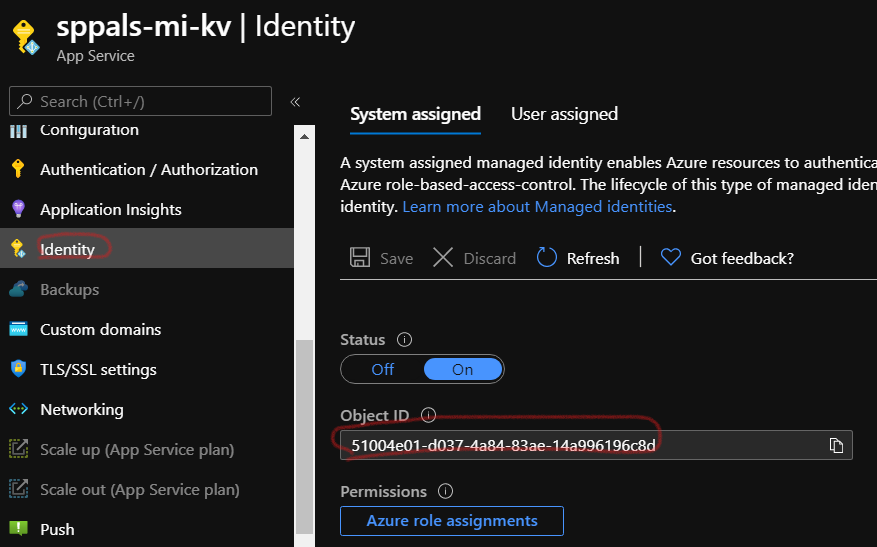
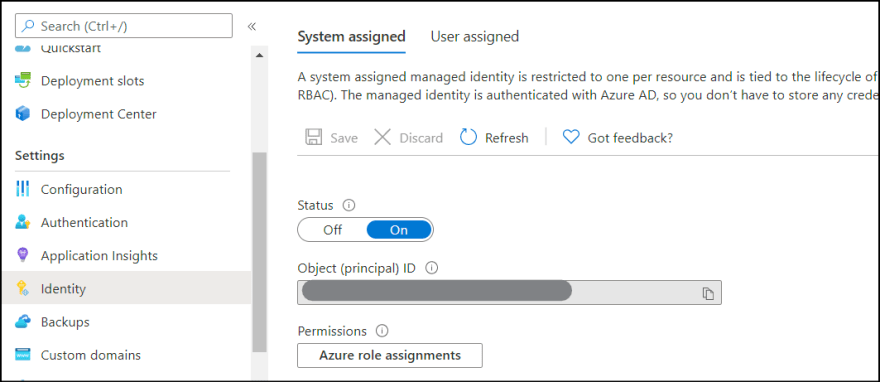
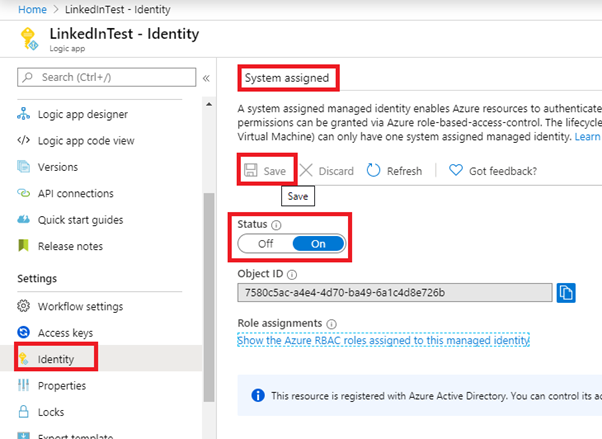
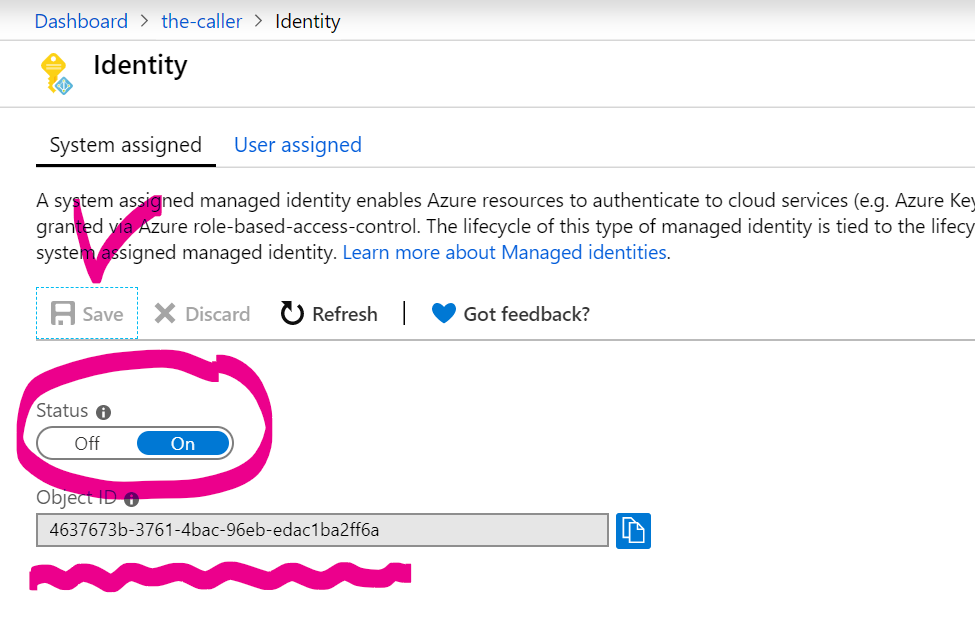
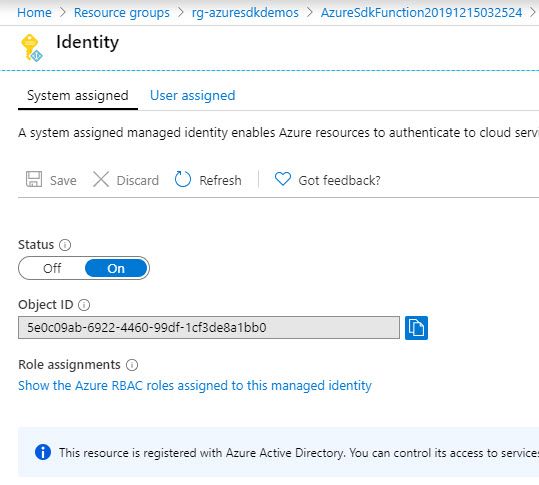
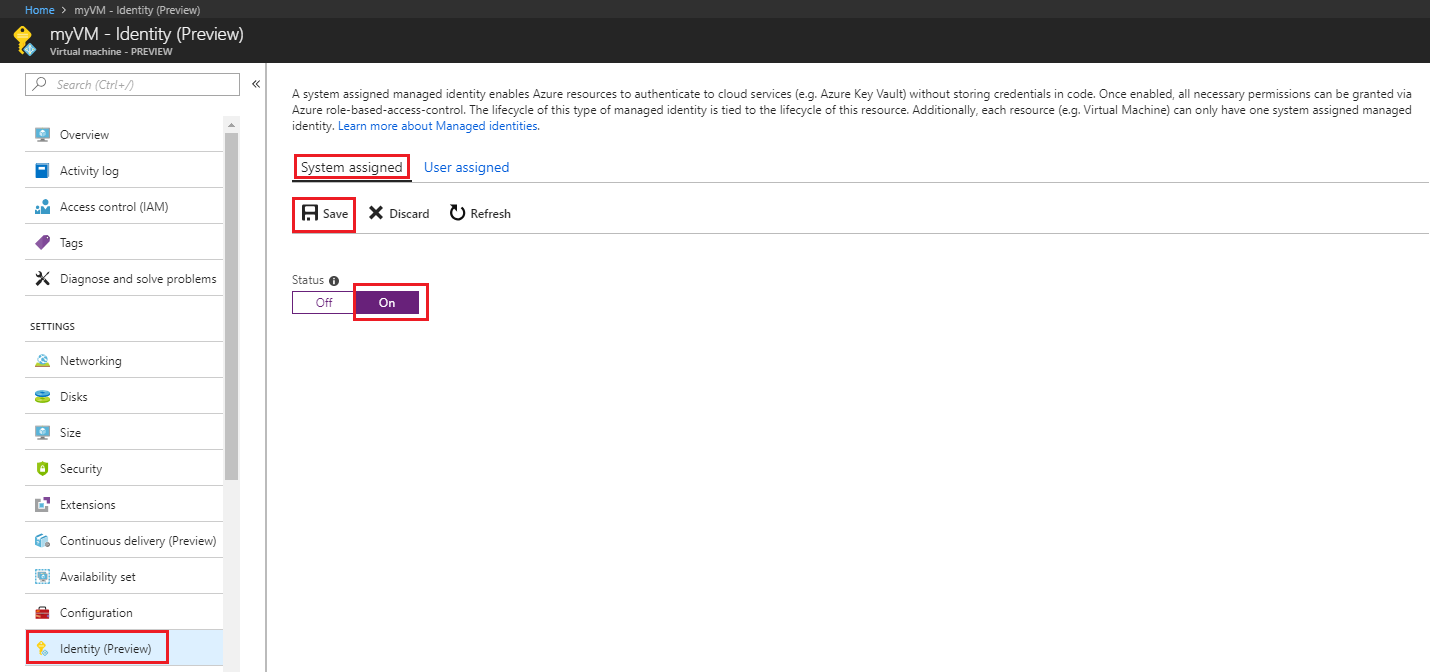
Under System assigned Status select On and then click Save. When the identity is enabled Azure creates an identity for the instance in the Azure AD tenant thats trusted by the subscription of the instance. Managed identities for Azure resources provide Azure services with an automatically managed identity in Azure AD.
System-Assigned Managed Identity vs. Once the system-assigned or user-assigned identities have been updated to managed identity run the following on your nodes to complete the update to managed identity. When you enable a system-assigned managed identity Azure creates an identity associated with the instance and stores it to the Azure AD tenant associated with the subscription where you created the service instance.
This article is based on system-assigned managed identities. At the time of writing May 2020 there is no option to assign such permission through the Azure Portal. Managed Identities are used for linking a Service Principal security object to an Azure Resource like a Virtual Machine Web App Logic App or similar.
This service is responsible for the authentication of Service Fabric applications using their managed identities and. There are two types of managed identities. When accessing the Microsoft Graph the managed identity needs to have proper permissions for the operation it wants to perform.
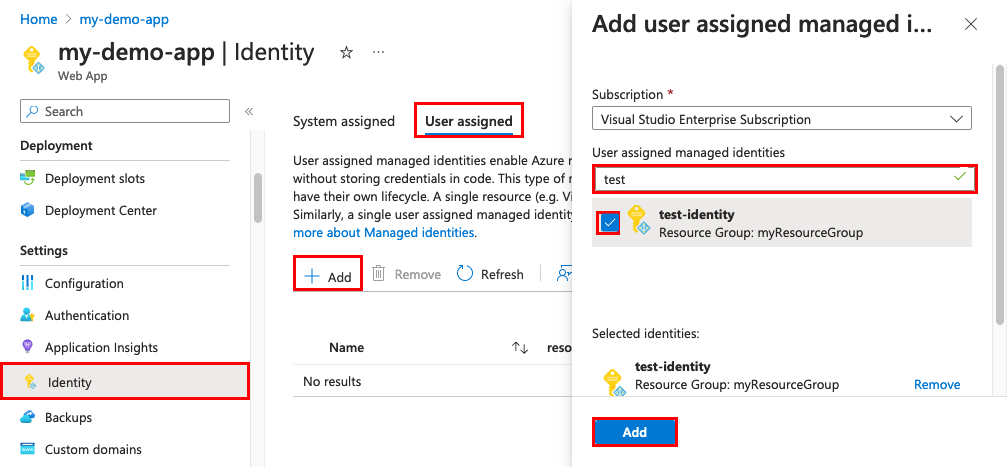
However I would now like to try using a managed identity instead so that the solution is more robust. User-Assigned Identity They are the same in the way they work. System-Assigned Azure Managed Identities provides a mechanism for the service in this case the Azure VM to have an identity instead of sharing the database credentials with a developer to embed in the application configuration file.
It eliminates the need to manage credentials by providing an identity for the Azure resource in Azure AD and using it to obtain Azure. For a 11 relation between both you would use a System Assigned where for a 1multi relation you would use a.
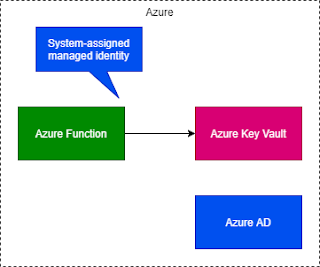
Managed identities work in conjunction with Azure Resource Manager ARM Azure AD and the Azure Instance Metadata Service IMDS.
In order to access the managed identity feature for Azure Service Fabric applications you must first enable the Managed Identity Token Service on the cluster. It is deleted automatically at. System assigned Managed Identities are automatically created along with the Azure resource and the life cycle of the managed identity depends on the Azure resource. Since the Function already has a managed identity AuditO365 Id like to replace the current user account with this identity in the custom role group in Exchange Online above but it appears that O365 cant see the managed identity. Managed Identities are used for linking a Service Principal security object to an Azure Resource like a Virtual Machine Web App Logic App or similar. When the identity is enabled Azure creates an identity for the instance in the Azure AD tenant thats trusted by the subscription of the instance. However I would now like to try using a managed identity instead so that the solution is more robust. It eliminates the need to manage credentials by providing an identity for the Azure resource in Azure AD and using it to obtain Azure. For the examples involving PowerShell first sign in to Azure interactively using the Connect-AzAccount cmdlet and follow the instructions.
For the examples involving PowerShell first sign in to Azure interactively using the Connect-AzAccount cmdlet and follow the instructions. This service is responsible for the authentication of Service Fabric applications using their managed identities and. System assigned and maintained identities enables the management of secrets and credentials to secure communication between different services. Managed Identities are used for linking a Service Principal security object to an Azure Resource like a Virtual Machine Web App Logic App or similar. System-Assigned Azure Managed Identities provides a mechanism for the service in this case the Azure VM to have an identity instead of sharing the database credentials with a developer to embed in the application configuration file. When accessing the Microsoft Graph the managed identity needs to have proper permissions for the operation it wants to perform. However I would now like to try using a managed identity instead so that the solution is more robust.




























Post a Comment for "System Assigned Managed Identity"